 Bring Your Own Device (BYOD) is making its way into every enterprise: from hospitals to higher education to corporations. So it’s no surprise that the demand by consumers for BYOD functionality is becoming prevalent in the hospitality industry as well. Guest’s personal devices are becoming faster, smarter and more personalized than ever before. The benefits derived from the plethora of applications and capabilities supported by these devices have become nearly essential to today’s business and leisure traveler. The increase in guest’s use of their own devices, however, has resulted in a disconnect between the hotel property and portions of the guest experience, primarily in voice communications. For example, telephone calls to hotel guests from staff or other guests, if gone unanswered, typically revert to a guest personal voicemail box. As a result, guests hanging out by the pool, restaurant or bar, or working in the conference center do not get the phone call and may go a long time before discovering that someone is trying to reach them. Therein lies the disconnect.
Bring Your Own Device (BYOD) is making its way into every enterprise: from hospitals to higher education to corporations. So it’s no surprise that the demand by consumers for BYOD functionality is becoming prevalent in the hospitality industry as well. Guest’s personal devices are becoming faster, smarter and more personalized than ever before. The benefits derived from the plethora of applications and capabilities supported by these devices have become nearly essential to today’s business and leisure traveler. The increase in guest’s use of their own devices, however, has resulted in a disconnect between the hotel property and portions of the guest experience, primarily in voice communications. For example, telephone calls to hotel guests from staff or other guests, if gone unanswered, typically revert to a guest personal voicemail box. As a result, guests hanging out by the pool, restaurant or bar, or working in the conference center do not get the phone call and may go a long time before discovering that someone is trying to reach them. Therein lies the disconnect.
In an attempt to improve the guest experience in the current environment, hotel companies are solving this dilemma by bridging the gap between the guest’s personal voice device and their own internal voice communication system. Since many guests typically prefer their own device and its personalized user interface, ringtones, contacts and functions, hotels can now easily make the guest’s device their primary extension during their stay at the hotel. Incoming calls to guests from within or outside of the hotel would ring on the personal mobile phone. A real advantage of this is that the guest does not have to be in their room to speak with the caller. The call will reach the guest anywhere on property as long as they have a cellular signal. For this simple but beneficial feature, guests provide their name and email address to the front desk agent of the hotel during the check-in process.
The benefits in implementing mobile technologies stack up for both hospitality managers and guests. By accommodating the guests’ device, you enhance guest engagement and improve customer satisfaction, which in turn can increase customer spending and revenue. The benefits certainly don’t stop there, mobile technology implementation can also accelerate guest traffic, give you a venue to promote sales of goods and services if you desire, and customer satisfaction surveys where you can gather feedback relative to the guest’s experience.
How can I use BYOD to enhance my guests’ experience?
The average consumer has access to advanced technology in their home, and has the same expectations when they travel. With this, hotels are under a lot of pressure to keep up with, and even exceed, the customer’s expectations. So what services can you offer your guests from their personal device?
- In-room dining ordering
- In-hotel restaurant listing and reservations
- Pre-arrival requests
- Mobile Payment options
- In-room environmental controls – lights, drapes, thermostat, TV, etc.
- Express check-out
- Hotel Area maps
……just to name a few
According to Pew Research, more than half of all mobile phone users rely on their portable device to search for information on hotels. With mobility, you can get everything you want, where you want, plus gain positive benefits in revenue, guest experience and marketing. With the steadily increasing volume of mobile network users, what better time for a hospitality business to embrace the guest BYOD trend and get them more connected to your business than ever before.
Check out our case studies to see how NEC has helped hotels around the world recover missed revenue opportunities, increase customer service, and enhance the overall guest experience.




 The increasing prevalence of mobile data has resulted in great security concerns for enterprises operating on multi-device systems, or with a Bring Your Own Device (BYOD) policy in place. It is challenging for businesses to decide whether the greatest value is in securing the devices that data is delivered to, or securing the data itself through methods such as Mobile Device Management (MDM). Mobile devices usage is highly favorable to end users in terms of access and convenience, but IT managers and CIOs cringe at the thought of the security risks associated with mobility and allowing sensitive data to be retrieved from virtually anywhere, any time. According to the
The increasing prevalence of mobile data has resulted in great security concerns for enterprises operating on multi-device systems, or with a Bring Your Own Device (BYOD) policy in place. It is challenging for businesses to decide whether the greatest value is in securing the devices that data is delivered to, or securing the data itself through methods such as Mobile Device Management (MDM). Mobile devices usage is highly favorable to end users in terms of access and convenience, but IT managers and CIOs cringe at the thought of the security risks associated with mobility and allowing sensitive data to be retrieved from virtually anywhere, any time. According to the 

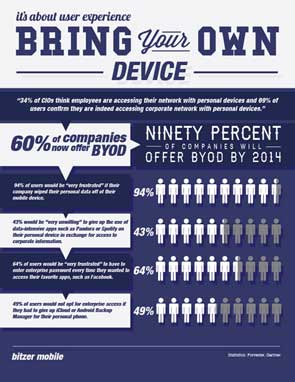 Smart phones, tablets, laptops, regardless of the device, the Bring Your Own Device, or BYOD phenomenon, is on the rise in organizations everywhere – even yours.
Smart phones, tablets, laptops, regardless of the device, the Bring Your Own Device, or BYOD phenomenon, is on the rise in organizations everywhere – even yours. 
 Unified Communications (UC) has enjoyed a steady, if not slow, broad acceptance as technology users begin to accept the efficiency and effectiveness of new market-driven apps. With employee mobility becoming a priority, an office for some does not include the traditional four walls, and as a result, smartphones and tablets have caused a rush for the door.
Unified Communications (UC) has enjoyed a steady, if not slow, broad acceptance as technology users begin to accept the efficiency and effectiveness of new market-driven apps. With employee mobility becoming a priority, an office for some does not include the traditional four walls, and as a result, smartphones and tablets have caused a rush for the door. Now that
Now that 
