This week while preparing for FETC 2015, I thought back to an article that Education Week published in December on digital content delivery and interoperability. With E-Learning software topping most educator’s shopping lists this year, interoperability is bound to be one of the many hot discussion topics heard on the exhibit floors during the show. So, I thought it might be a good idea to revisit the article here.
A handful of large school districts (like Houston Independent School District) have begun aggressively pushing big publishers of education-based digital content to begin revamping the way they deliver instructional materials—a movement which will upend the long-established purchasing patterns that typically keep educators from accessing materials from other vendors.
The movement is reminiscent of several interoperability debates in the IT/Tech world right now, and we’re seeing many school districts lead the charge in declaring that they will not do business with publishers who refuse to become interoperable.
It’s a huge step on the part of the school districts. A shift towards interoperability means many things. It can revolutionize how content-delivery systems interact with each other. It could also transform how schools purchase and consume digital content, allowing districts to procure small "chunks" of content (individual chapters, lessons or videos, for example) from multiple vendors, perhaps through licensing agreements, rather than rely on yearlong or grade-span textbook series from a single publisher.
Finding Interoperability
As FETC helps kick off trade show season and as school districts start moving into 2015, it may be time to begin evaluating content technologies that can easily manage both the interoperable content coming from publishers as well as any other content types/formats.
Here are a few things to look for as you begin to evaluate new content distribution platforms:
“Create-ivity” and Customizability
Content distribution platforms (a.k.a. Learning Management Systems) traditionally employ a structured sequential learning method that drives students to move through class material in a predefined order. The best interoperable technologies are going to offer more by way of on-demand flexibility—letting teachers either create or select content relevant to each student’s learning experience, helping achieve the best possible results in the classroom.
A fully interoperable, flexible content management and distribution solution should give professors and students the option to employ either a traditional sequential learning model or the ability create a truly customized learning experience by accessing individual content pieces in multiple formats (video, presentation, documents, etc.) that the school has either licensed from multiple publishers or created on its own.
Collaboration and Interactivity
There is an increased focus on collaboration in higher education in order to prepare students for today’s collaborative and adaptive work environments. The right Learning Management System should provide the social interaction to which students have become accustomed, and should include tools that allow students and teachers to create discussion feeds and workgroups for classroom-based conversations and project-based learning.
Today’s Learning Management Systems should allow students to work collaboratively and efficiently together in real-time to complete class assignments and projects, and also include tools that allow interactive experiences with the course content, including online components and hybrid learning strategies for flipped-classroom style learning.
“Integrate-ability” and Modernity
There are many challenges facing educators as classroom technology continues to advance. That’s why a content distribution platform should be easy to use, should integrate existing educational resources, and should be integrate-able with your existing district technologies (think Unified Communications solutions, virtualized or cloud storage systems, or analytics technologies).
Collaborative Content Management
School districts like Houston’s are drawing lines in the sand—demanding more from the publishers creating K-12 content. The same demands will now need to be made of the technologists creating the distribution solutions.
That said, NEC is going to be at FETC this week demoing several of our education solutions—including our Collaborative Content Management solution, a cloud-based Learning Management System which is fully interoperable, flexible, and collaborative right out of the box.
If you’d like to learn more about NEC’s Collaborative Content Management before the show, check out our webinar below.
If you happen to be at FETC this week, stop by booth #1268 to chat with an NEC expert during normal Expo hours.


 With all the negative reporting around economic recoveries, it’s always nice to hear a little good news. Each year, hoteliers around the world see larger chunks of money spent on travel. In 2013, Americans spent
With all the negative reporting around economic recoveries, it’s always nice to hear a little good news. Each year, hoteliers around the world see larger chunks of money spent on travel. In 2013, Americans spent 

 Mobile devices are completely ingrained in our daily lives. They entertain, remind, socialize, and manage us. They are our personal authentication key to the world around us. They are an extension of ourselves. Handheld mobile devices are just extremely personal, more so than any other device we interact with during the day. When asked, most people will say that they’ll give up food or sleep before they’re deprived of their mobile device, and for most there is a discernable level of anxiety when their device isn’t actively with them.
Mobile devices are completely ingrained in our daily lives. They entertain, remind, socialize, and manage us. They are our personal authentication key to the world around us. They are an extension of ourselves. Handheld mobile devices are just extremely personal, more so than any other device we interact with during the day. When asked, most people will say that they’ll give up food or sleep before they’re deprived of their mobile device, and for most there is a discernable level of anxiety when their device isn’t actively with them.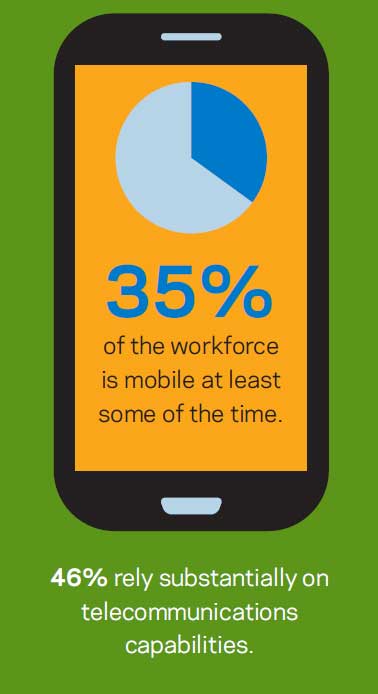 The personal dynamics of mobile devices and, in turn, mobile device management, has made adoption of mobile technology a tricky business across the board. For most organizations, Bring Your Own Device (BYOD) policies are still complex and perceived as risky. But, with the global workforce’s rapid adoption of the mobile work style, integration of BYOD policies have been necessary for most organizations to maintain the high levels of productivity needed to sustain business success. In fact, only businesses with high-level security concerns and strict privacy needs—like financial organizations—can succeed in today’s marketplace without some form of acceptance of BYOD in their mobile policies.
The personal dynamics of mobile devices and, in turn, mobile device management, has made adoption of mobile technology a tricky business across the board. For most organizations, Bring Your Own Device (BYOD) policies are still complex and perceived as risky. But, with the global workforce’s rapid adoption of the mobile work style, integration of BYOD policies have been necessary for most organizations to maintain the high levels of productivity needed to sustain business success. In fact, only businesses with high-level security concerns and strict privacy needs—like financial organizations—can succeed in today’s marketplace without some form of acceptance of BYOD in their mobile policies. The key challenges for businesses of all sizes adopting cloud and mobility applications is finding the right balance between usability and data security. In an ideal world, users would like to have one-click access to an increasing number of apps without needing 12 digit passwords for each app. Since users are bringing in their own devices, and these devices are the primary means to app access, they must be “trusted” within the organization and secured.
The key challenges for businesses of all sizes adopting cloud and mobility applications is finding the right balance between usability and data security. In an ideal world, users would like to have one-click access to an increasing number of apps without needing 12 digit passwords for each app. Since users are bringing in their own devices, and these devices are the primary means to app access, they must be “trusted” within the organization and secured.
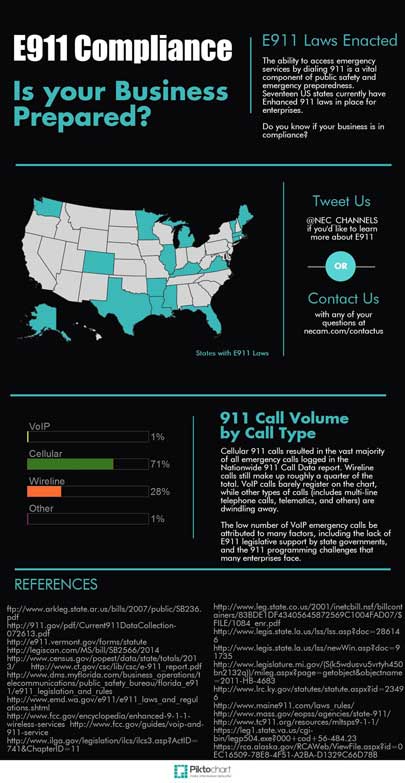
 The need for modernization among IT departments is a trend that is becoming increasingly relevant as IT departments are constantly faced with generational shifts in technology. The pressures of modern business require that IT departments close the gap between yesterday’s IT implementations and tomorrow’s demands.
The need for modernization among IT departments is a trend that is becoming increasingly relevant as IT departments are constantly faced with generational shifts in technology. The pressures of modern business require that IT departments close the gap between yesterday’s IT implementations and tomorrow’s demands. The productivity benefits of
The productivity benefits of 
 HITEC begins today, and our NEC hospitality team is looking forward to the trends that we will be seeing on the show floor. Here are some of our predictions:
HITEC begins today, and our NEC hospitality team is looking forward to the trends that we will be seeing on the show floor. Here are some of our predictions: